DogWifTools Hacking Incident: A Security Wake-Up Call for the Solana Community
DogWifTools Hacking Incident: A Security Wake-Up Call for the Solana Community
In January 2025, DogWifTools users faced a nightmare. As a widely used tool for faking liquidity to facilitate rug pulls on the Solana blockchain, DogWifTools was originally designed to create illusions for scammers. However, attackers exploited malicious code embedded in the tool to take revenge on users by stealing sensitive data from their computers and siphoning off approximately $10 million in crypto assets from their wallets.
Details of the Attack
Supply Chain Attack Overview
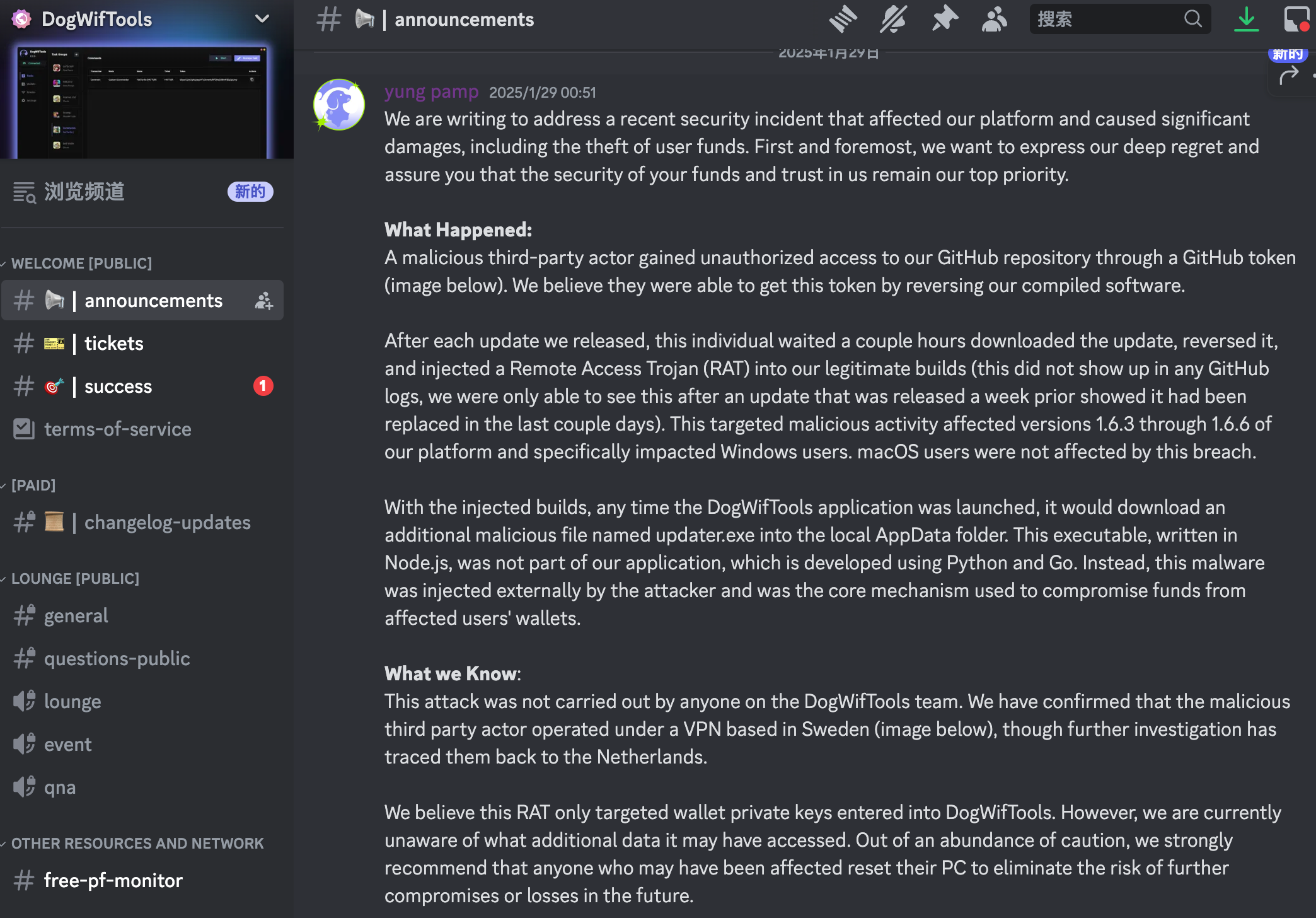
Attackers reverse-engineered the DogWifTools GitHub repository to extract a GitHub token, which granted them write access. With this access, they updated a new version just a few hours after the release of versions 1.6.3 through 1.6.6, stealthily injecting a Remote Access Trojan (RAT) into the build. This supply chain attack method highlights a major cybersecurity concern: attackers leveraging legitimate update processes to covertly embed malicious code and steal private keys, login credentials, and users’ identity information.
Functionality and Consequences of the Trojan
The injected RAT was capable of scanning users’ systems to collect sensitive data, including blockchain private keys, crypto exchange login credentials, and users’ identity documents. Using this information, attackers not only stole large amounts of crypto assets from victims' wallets, but also misappropriated identities by using the stolen documents to pass KYC checks on exchanges like Binance, subsequently withdrawing the stolen funds.
The Attacker’s Justification
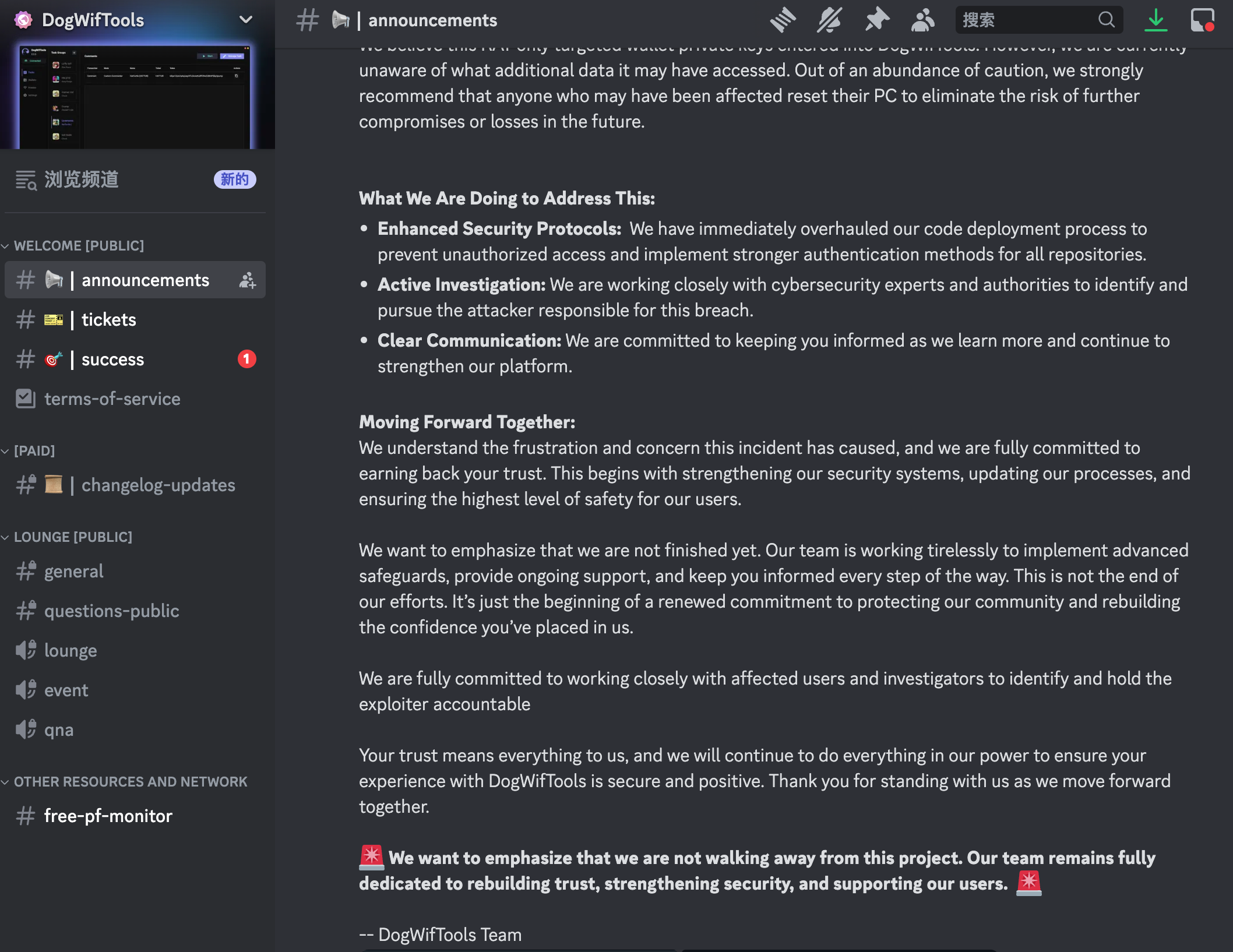
In a manifesto published on TOR, the attacker claimed that all victims were scammers, arguing that this “revenge” was morally justified. Although this justification is hard to accept, the incident undoubtedly exposed serious flaws in permission management and code security on the part of the developers.
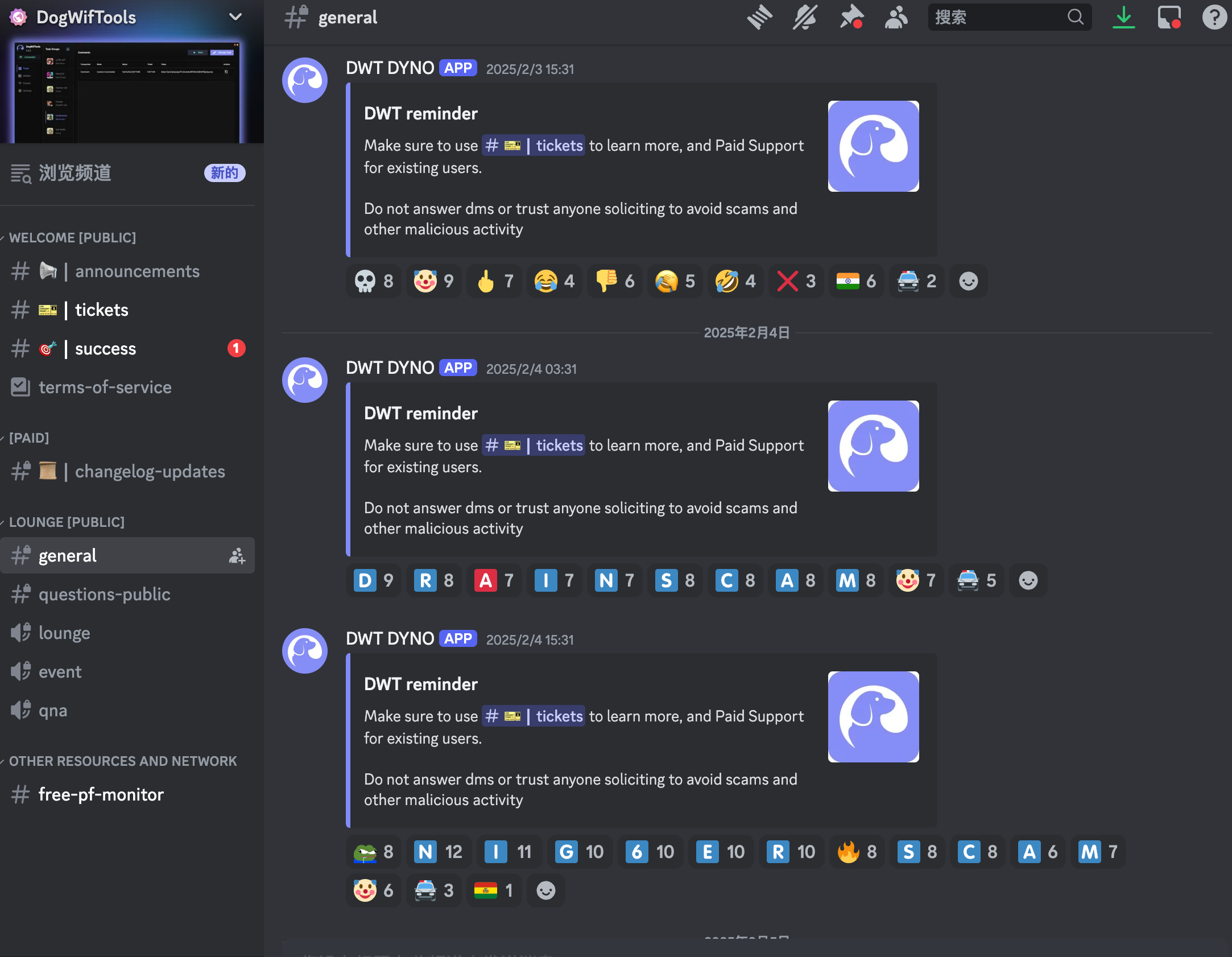
The Dogwiftools community has been silenced, but users are still venting their anger through emojis:
Dogwiftools Official Statement:
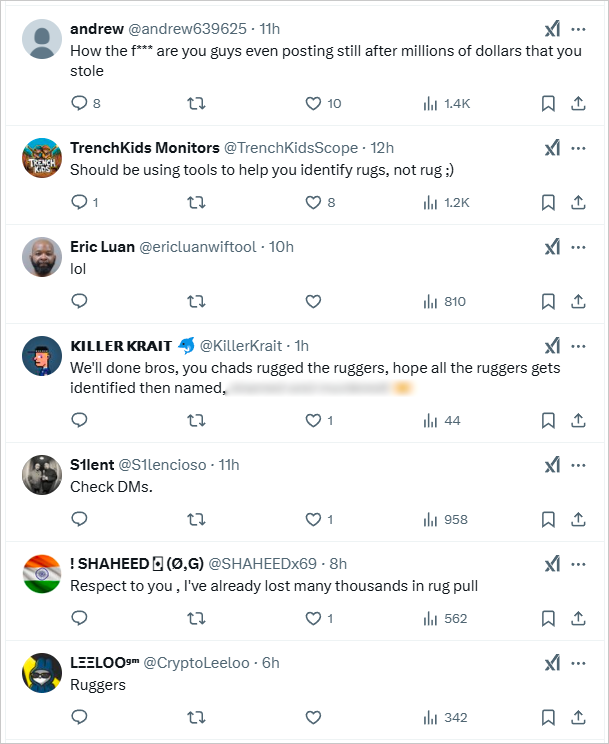
Anger from Twitter Users
DogWifTools official statements and community reactions, especially on Discord—where users expressed their anger through emojis as the community had been silenced—reflect the deep frustration among users.
How to Choose Secure and Reliable Solana On-chain Tools
The DogWifTools incident serves as a wake-up call for the entire community. For on-chain tools—especially those involving wallet signatures and asset management—security and transparency are paramount. Consider the following guidelines when selecting and evaluating such tools:
- Prioritize Browser-based Web Tools
For instance, slerftools is a browser-based tool. Compared to software that requires installation, web tools offer higher security and transparency:- Enhanced Wallet Signature Security: Signing transactions through a browser means private keys do not need to be exposed on local software, reducing the risk of theft by malicious software.
- More Transparent Process: Users can directly view transaction details in the browser, with all interactions open and auditable, facilitating easier monitoring and security checks.
- User Base and Credibility are Critical
Choosing tools with a large user base and a long-standing reputation can significantly reduce risks:- Trust from Extensive Use: Since its launch, slerftools has serviced tens of millions of transactions, demonstrating that its development team’s technical and security measures have been rigorously tested over time.
- A Mature Development Community: Popular tools usually offer comprehensive support, rapid vulnerability responses, and transparent development processes. In contrast, niche tools with fewer users may lack sufficient validation and be more prone to security issues.
- Permission Management and Security Audits are Essential
- Review the Permissions Requested: Before installing any tool, carefully check the permissions it requests. If a tool demands high-risk permissions unrelated to its functionality, proceed with caution.
- Stay Updated with Security Announcements: Developers should regularly publish security audit reports, and users need to keep an eye on community discussions and feedback regarding tool security to avoid incidents like the DogWifTools attack.
Conclusion
The DogWifTools case demonstrates that even tools designed for illicit activities can backfire due to security vulnerabilities. For Solana users and developers, increasing vigilance, enforcing strict permission management, and choosing on-chain tools with a robust and verified user base are essential measures for safeguarding digital assets. Only by continuously improving technical security and transparency can the crypto ecosystem build a robust defense against future threats.